Identity Access Management (IAM)
Secure your digital assets with enterprise-grade IAM solutions designed to control access, prevent breaches, and ensure compliance.
CyberAuths IAM
- Adaptive MFA
- Least privilege access
- Customizable & Advance workflows
- Real-Time Threat Detection & Response
Why Choose Our IAM?
- Zero Trust Architecture
- Role-Based Access Control
- Compliance Ready (GDPR, HIPAA)
- Real-Time Threat Monitoring
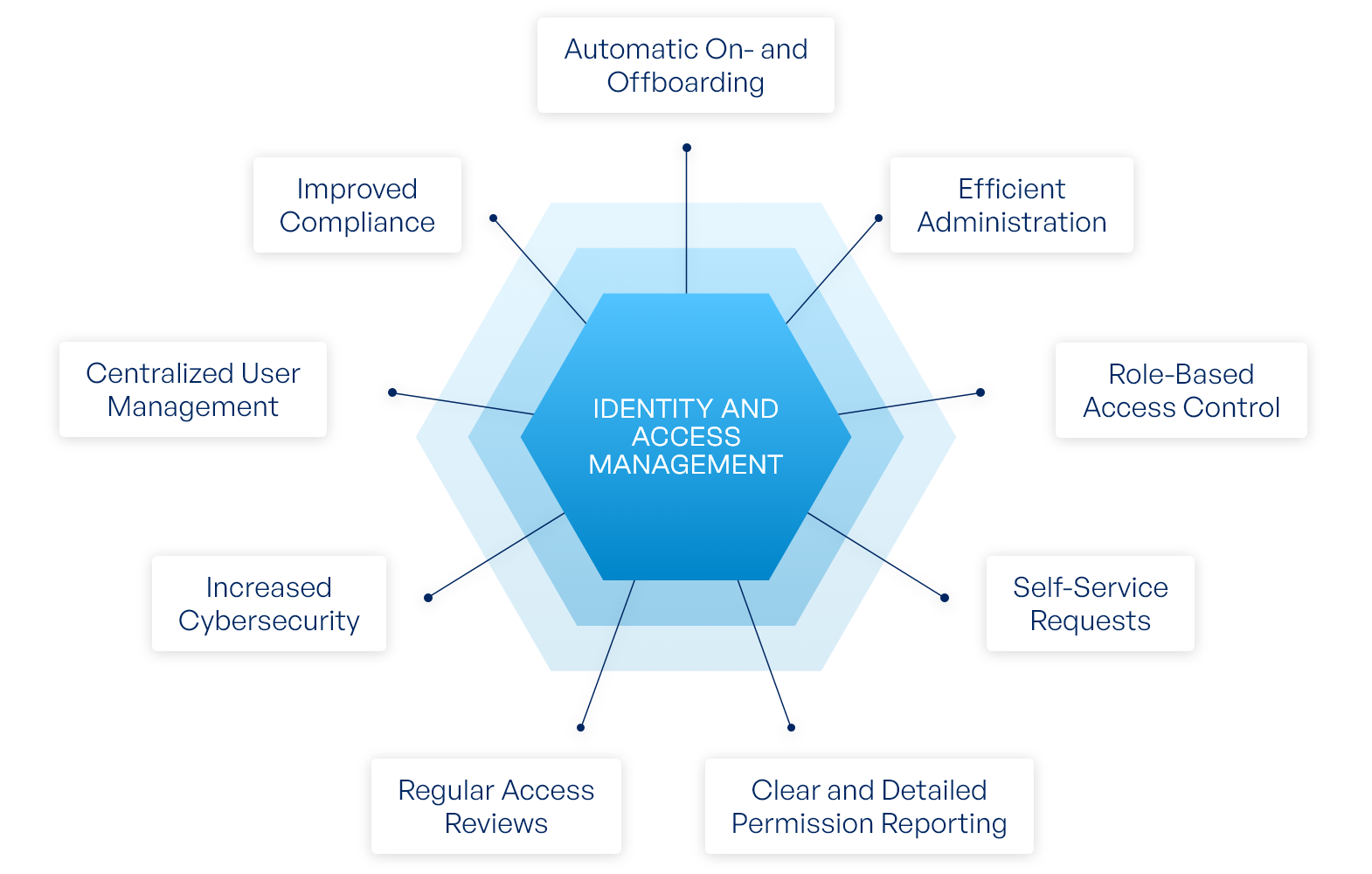
Enterprise-Grade Access Control
CyberAuths’ IAM solutions provide granular control over user access across your applications, data, and infrastructure. Our multi-layered approach combines MFA (Multi-Factor Authentication), SSO (Single Sign-On), and privileged access management to minimize attack surfaces and prevent unauthorized access.
Key Features
- Dynamic Access Policies: Context-aware rules based on user role, location, and device.
- Seamless Integration: Works with Active Directory, Okta, and custom apps.
- Audit Trails: Detailed logs for compliance reporting and forensic analysis.
Implementation Process
Assessment
Analyze your current access controls and identify vulnerabilities.
Customization
Design tailored IAM policies aligned with your workflows.
Deployment
Phased rollout with minimal disruption to operations.
Core IAM Capabilities
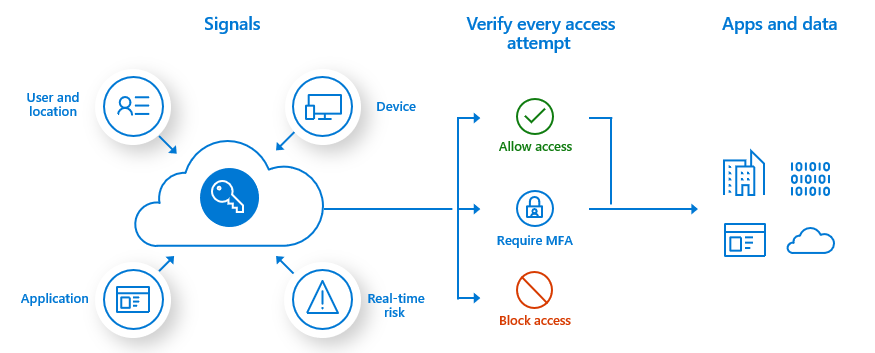
Multi-Factor Authentication
Combine passwords with biometrics, SMS codes, or hardware tokens to block 99.9% of credential attacks.
- Adaptive risk-based authentication
- FIDO2 compliant
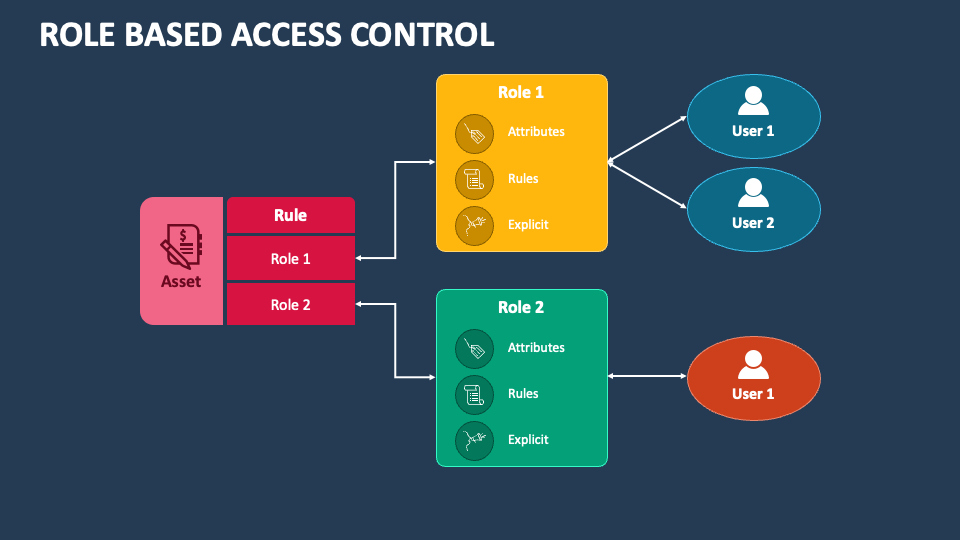
Granular Access Control
Implement least-privilege policies with customizable roles and permissions.
- Department-specific access tiers
- Temporary privilege escalation
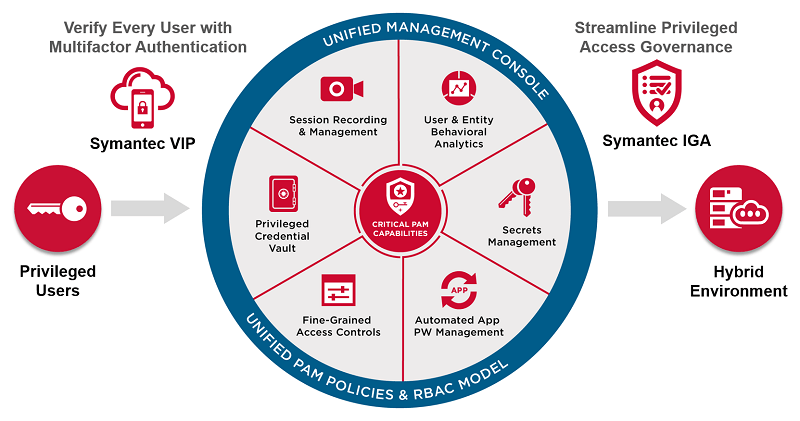
Privileged Access Security
Secure admin accounts with just-in-time access and session monitoring to prevent insider threats.
- Session recording & audit trails
- Automated credential rotation

Behavioral Threat Detection
AI-driven anomaly detection identifies compromised accounts 3x faster than traditional methods.
- Real-time risk scoring
- Automated response workflows

Global Bank Reduces Breaches by 92%
After implementing CyberAuths IAM, this Fortune 500 bank eliminated credential stuffing attacks and streamlined employee access.